A group of researchers from four American universities developed an attack technique Pixnapping (CVE-2025-48561), allowing unprivileged Android applications that do not request additional permissions to determine the content displayed by other applications. As an example of a practical application of the attack, the detection of two-factor authentication codes displayed by the Google Authenticator application was demonstrated. It also shows how the attack can be used to extract confidential data displayed on the screen when working with Gmail, Signal, Venmo and Google Maps.
To determine the contents of the screen, a pixel-by-pixel analysis method was used, implemented in 2023 by the same team of researchers in the GPU.zip side-channel attack and for the first time described back in 2013. The essence of the method is that, due to the optimizations present in the GPU, rendering a pixel with a color that repeats the color already displayed on the screen is faster than a pixel with a different color. By assessing the difference in time when drawing pixels, you can recreate the content already on the screen and form a semblance of a screenshot.
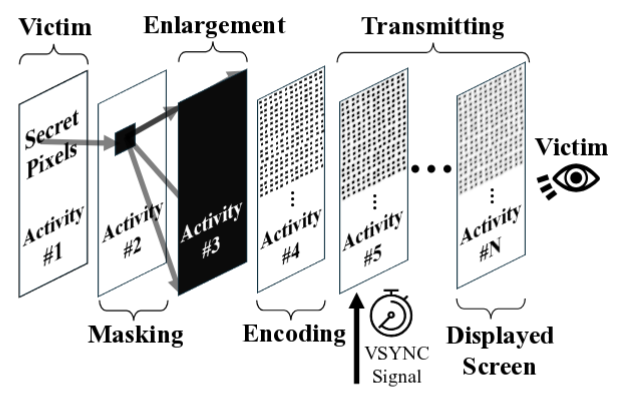
The Pixnapping attack comes down to calling the target application, displaying your window on top of it, and pixel-by-pixel iterating through the content, analyzing the time it takes to perform graphical operations on each pixel. Such an enumeration makes it possible to determine with high probability which pixels have a white background color and which are involved in displaying characters. To hide manipulations with pixels from the user, layers with masks are applied – during the attack, the contents of the application window from which the attack is carried out continue to be visually shown on the screen.
To activate the attacked application and get pixels from its window into the rendering pipeline, switch between Android activities using intent-queries. Translucent windows are displayed on top of the attacked application window, highlighting individual pixels and initiating graphic operations on them using the Window Blurs API. Callback calls tied to VSync are used to measure the exact time a pixel is drawn.