In the WordPress plugin Easy WP SMTP , designed to organize sending emails through an SMTP server and with over 500 thousand active installations, detected a vulnerability allowing full access to the site with administrator rights. The issue was fixed in the 1.4.4 release. It is noteworthy that the developers learned about the problem after a massive attack on sites with this plugin, during which unknown attackers changed the administrator password (a 0-day vulnerability used for the attack before the patch was released).
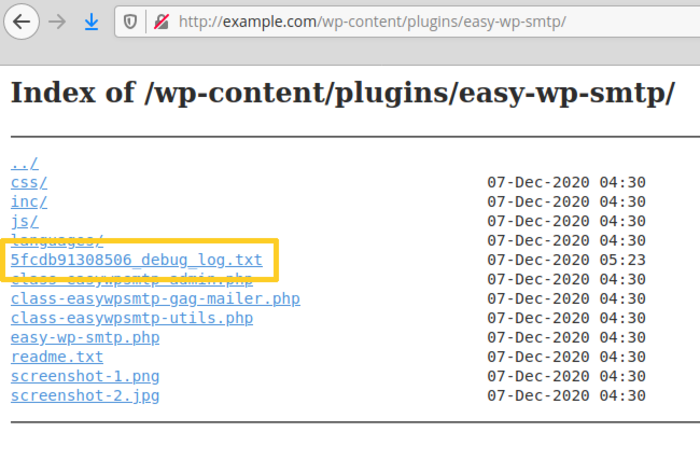
The vulnerability was caused by that the plugin saved a debug log file in the publicly accessible directory “/ wp-content / plugins / easy-wp-smtp /”, which displayed the contents of all sent emails. The log was created with random characters in the file name (for example, “5fcdb91308506_debug_log.txt”), but the directory was not configured to hide the file list. In release 1.4.3, the developers added an index.html file to prohibit viewing the list of files, and in release 1.4.4, they moved the log to a separate directory and added a content reset every time the plugin was activated.
For the attack, it was enough to initiate on the site is the process of recovering a forgotten password for a user with administrator rights, after which an email with a password reset code was sent to the real administrator. The attacker could see the contents of this letter and the link to the password change form in the debug log.
 a >
a > 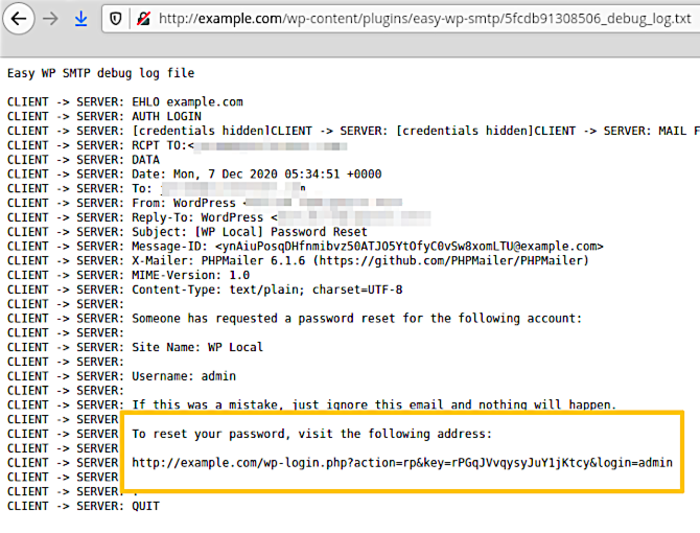
You can additionally mark new release of the web content management system WordPress 5.6