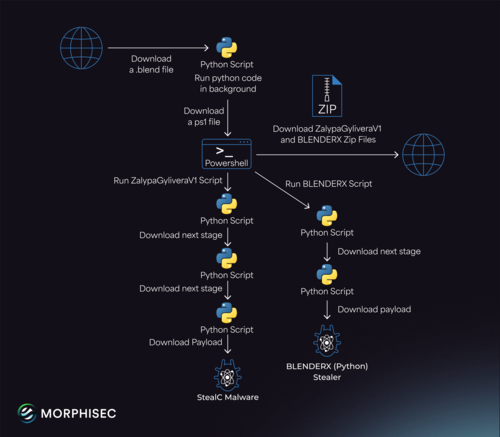
Security researchers from Morphisec have uncovered a series of attacks targeting users of the Blender 3D modeling system. These attacks were carried out through the distribution of blend files in popular 3D model directories such as CGTrader. The malicious code is activated when opening a 3D model, leveraging the ability to include automatically launched scripts in Python within blend files. These scripts are designed to automate actions and perform advanced operations, such as forming a model skeleton.
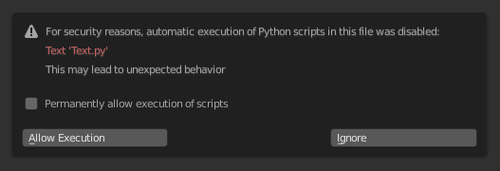
The primary targets of this attack are users who have enabled the option to automatically launch scripts from blend files. While automatic launch is disabled by default, users can easily confirm the launch in a warning dialog or change the default settings. The malicious blend files may not immediately raise suspicion, as they offer popular working models like 3D spacesuits, accompanied by a Python script, Rig_Ui.py, which includes a well-known implementation of an automatic rigging system.
In one identified blend file, researchers discovered that the legitimate version of Rig_Ui.py had been modified to load and run the StealC V2 malware. To conceal its tracks, the malware was downloaded through the intermediate site blenderxnew.tohocaper1979.workers.dev, utilizing the Cloudflare Workers platform. Sensitive data found on the system was then sent in encrypted form. It’s important to note that the malware specifically targets Windows users.
Once activated, StealC V2 remains on the system, intercepting, searching for, and sending sensitive data such as access tokens, encryption keys, and passwords. It has the capability to extract confidential data from 15 crypto wallets, over 100 browser add-ons related to cryptocurrencies and payment systems, 23 different browsers, instant messengers like Telegram and Discord, VPN services such as ProtonVPN and OpenVPN, as well as email clients including Thunderbird.