Researchers from the University of Cambridge Published new TECHNOEC An invaluable malware substitution to peer-reviewed source texts. Prepared Attack method ( CVE-2021-42574 ) is presented under the name Trojan Source and based on the formation of text in different ways looking for a compiler / interpreter and a person looking through the code. Examples of the application of the for various compilers and interpreters supplied for Languages C, C ++, C #, JavaScript, Java, Rust, Go and python.
The method is based on application in comments to the code of special Unicode characters, changing the procedure for displaying bidirectional text. With the help of such control characters, some parts of the text can be outlined from left to right, while other on the right left. Thus, with the help of the text displaced, the ongoing-left can be overlapped already existing conventional text displayed from left to right.
Using this method in the code, you can add a malicious design, but then in the next commentary comments make text with this design imperceptible when viewing the code, through the addition of the characters, shown on the right, which will lead to the imposition of a malicious insertion Other characters. Such code will remain semantically correct, but will be interpreted differently and displayed.
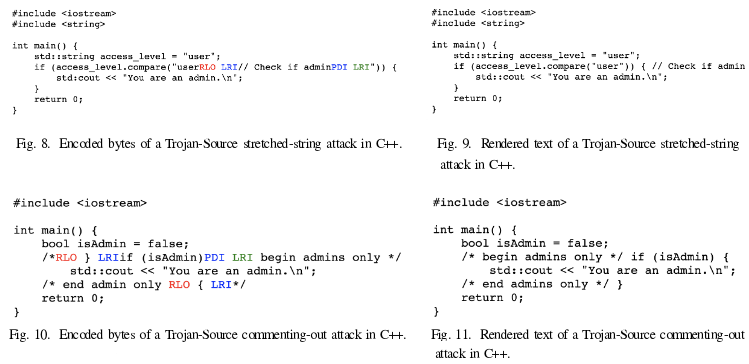
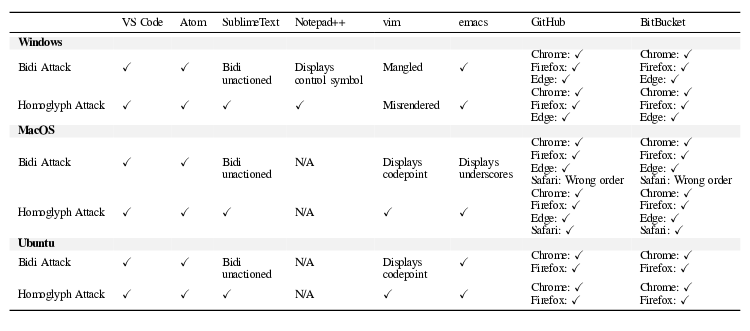
In the process of reviewing the code, the developer will collide with the visual procedure for outputting characters and sees in the modern text editor, web-interface or IDE does not cause suspicion comment, but the compiler and the interpreter will use the logical order of characters and processes the malicious insert as there is no paying attention On bidirectional text in the comments. The problem is subject to various popular code editors (VS Code, Emacs, Atom), as well as interfaces for viewing the code in repositories (Githib, Bitbucket).
There are several ways to use the method for implementing malicious actions: adding a hidden “Return” expression, which leads to the completion of the function before the function; conclusion in the comment of expressions, normally visible as active structures (for example, to disable important checks); Assigning other string values leading to lines check failures.
For example, an attacker can offer a change, including a string: