Engineers from Intel offered New HTTPA protocol (HTTPS Attestable), expanding HTTPS with additional security guarantees of the computing. HTTPA allows you to guarantee the integrity of the user’s request processing and make sure that the Web service deserves trust and working in Tee – TRUSTED Execution Environment) On the server code was not changed as a result of hacking or administrator diversion.
httpS protects the transmitted data at the transfer phase over the network, but cannot exclude the violation of their integrity as a result of attacks on the computing environment. Isolated enclaves created using technologies such as Intel SGX (Software Guard Extension), ARM TrustZone and AMD PSP (Platform Security Processor) make it possible to protect important calculations and reduce the risk of leaks or change confidential information on the end node.
http to guarantee the reliability of the transmitted information allows you to use the means provided in Intel SGX Certification , confirming the authenticity of the anklav, in which calculations are made, as well as the manufacturer and verification process. In essence, HTTPA expands HTTPS the possibility of remote enclave certification and allows you to check that it is performed in a genuine surrounding Intel SGX and the Web service can be trusted. The protocol is initially developing as universal and in addition to Intel SGX can be implemented for other TEE systems.
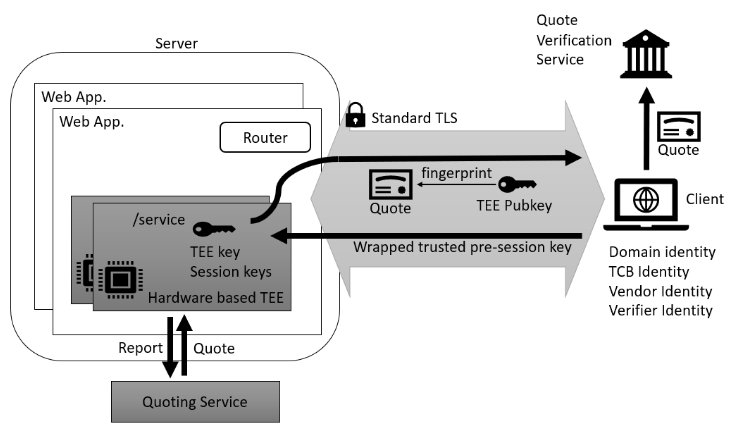
In addition to the HTTPS process of installing a secure connection, HTTPA additionally requires the coordination of the session key deserving confidence. The protocol introduces the new HTTP method “Attest” to use, which allows you to handle three types of requests and answers:
- “Preflight” to verify whether the remote side supports the certification of enclaves;
- “attest” to match the parameters of the certification (selection of the cryptographic algorithm, the exchange of unique for sessions by random sequences, generating a session identifier and the application of the open key of the enclave);
- “Trusted Session” – the formation of a session key for trusting information. The session key is formed on the basis of a previously agreed preliminary secret sequence (Pre-Session Secret), formed by the client using the TEE open key received from the open key server, and generated by each side of random sequences.