In the NPM package PAC-RESOLVER , numbering more than 3 million downloads per week, vulnerability (CVE-2021-23406), which allows you to achieve your JavaScript code in the context of the application when sending http -Frishes from node.js projects supporting the control server auto-tuning function.
PAC-RESOLVER packages PAC files , including the script for automatic proxy server setting. The PAC file contains a normal JavaScript code with the FindProxyForull function that defines the proxy selection logic depending on the host and the requested URL. The essence of the vulnerability is that to perform this JavaScript code to the PAC-RESOLVER used in Node.js API vm ,
Allows you to execute JavaScript code in another context of the V8 engine.
The specified API is clearly marked in the documentation as not intended to start a code that does not trust, since it does not provide a full-fledged isolation of the started code and allows access to the original context. This issue is addressed in the release of pac-resolver 5.0.0, which is transferred to the use of the library vm2 providing a higher level of insulation suitable for running non-credible code.
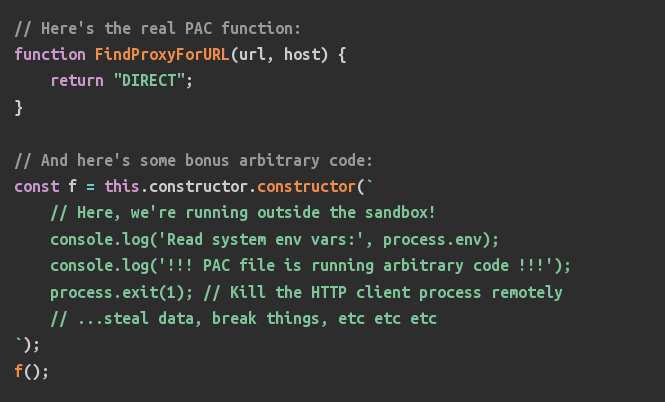
When using the PAC-RESOLVER vulnerable version, an attacker through the transmission of a specially decorated PAC file can make the execution of its JavaScript code in the context of the project code using Node.js, if the Proxy-Agent , Specified depending on 360 projects, including URLLIB, AWS-CDK, Mailgun.js and Firebase-Tools, which have more than a hundred thousand downloads per week.
If the application associated with the PAC-RESOLVER adds is loaded by the PAC file, a resource with support for the automatic proxy setup protocol WPAD , to substitute malicious PAC files, intruders who have access to a local network can use the distribution of proxy settings via DHCP.